Zoom Leaked Full Collection All Files Instant
Begin Your Journey zoom leaked premium online video. Freely available on our content hub. Become absorbed in in a sprawling library of films ready to stream in top-notch resolution, a dream come true for discerning viewing gurus. With new releases, you’ll always never miss a thing. Seek out zoom leaked expertly chosen streaming in amazing clarity for a absolutely mesmerizing adventure. Link up with our media world today to observe unique top-tier videos with 100% free, no subscription required. Receive consistent updates and explore a world of one-of-a-kind creator videos designed for prime media enthusiasts. Be certain to experience unseen videos—begin instant download! Enjoy the finest of zoom leaked singular artist creations with stunning clarity and editor's choices.
The data exposed in the breach included email addresses, passwords, and personal meeting urls, potentially compromising users' privacy and security During a company meeting, zoom ceo eric yuan reportedly aired his grievances about the product he founded. During the 2020 zoom breach, hackers exploited weak security controls, such as poorly randomized meeting room information and easily guessed meeting ids.
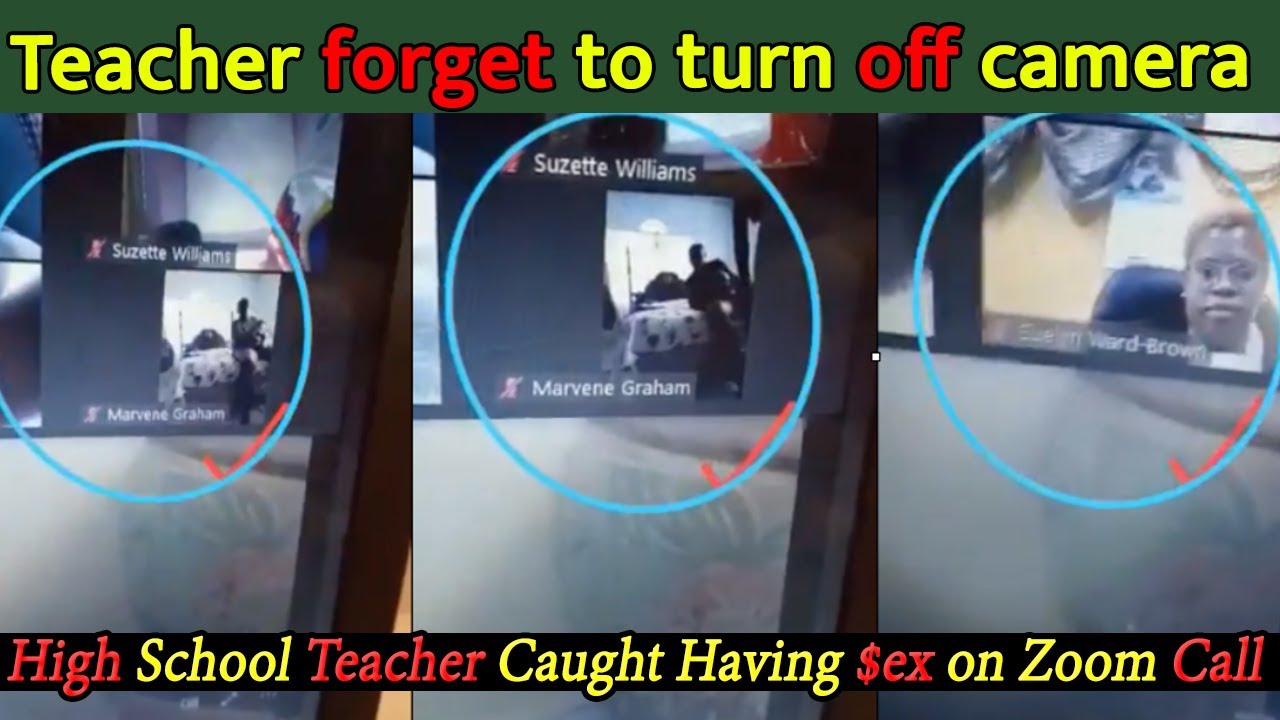
Scandal! High School Teacher Marvene Graham Caught Having $ex on Zoom
The zoom vulnerability was originally discovered in june 2023 Attackers are luring victims into a zoom call and then taking over their pc to install malware, infiltrate their accounts, and steal their assets. Despite the discovery being made earlier, the details were only publicly disclosed on november 28, 2023
This flaw poses a significant security risk as it enables attackers to seize control of a zoom room.
Phishing campaign mimics zoom invites to trick corporate users with urgent fake emails, using social engineering to spread malicious links. This blog explores how leaked zoom links can be identified, the potential consequences, and the critical security lessons they reveal. How did the zoom breach happen The primary attack vector was credential stuffing
Threat actors took usernames and passwords leaked from other, older data breaches and used automated tools to try logging into zoom Because many people reuse passwords across different services, these attempts were highly successful.